Our founder Simon Moffatt will be moderating a panel at the Future Identity conference in London […]
Our Founder and Research Analyst Simon Moffatt will be in attendance at this year’s RSA Conference […]
Next week The Cyber Hut founder and research analyst Simon Moffatt will be hosting an industry […]
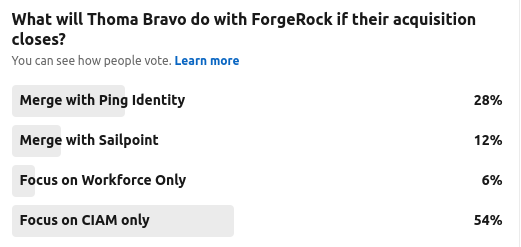
An opinion piece analysing the potential acquisition of ForgeRock by private equity firm Thoma Bravo.
Last week I had the pleasure of presenting a rapid and remote 10 minute keynote at the southern LATAM IAM Tech Day Event.
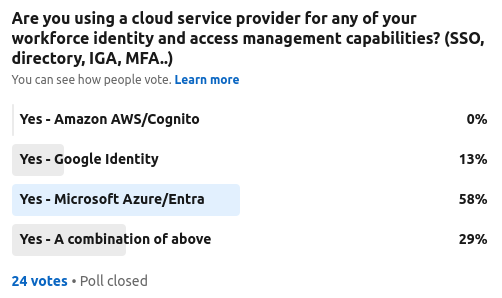
A review of the recent re-brand of Microsoft Entra for their IAM capabilities and the results of two community polls relating to Microsoft adoption.
Join our founder and industry analyst Simon Moffatt on February 21st, where he will be in conversation with Jonathan Fussner from zero-trust identity and access management startup Cyberelements.
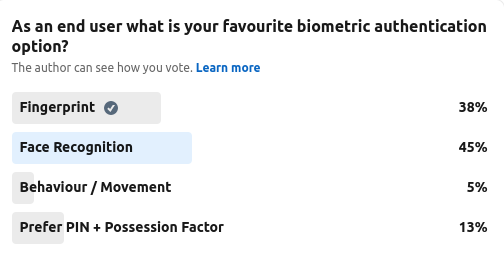
As part of The Cyber Hut's anecdotal community polls, we asked as an end user, what is your favourite biometric authentication option? The rise of device specific biometry to unlock our Android and iPhone based devices has increased in the last 3 years and many smart phone users will chose this over a basic PIN (albeit PIN is likely still needed after a hard reset).
I'm proud to announce today, the latest addition to The Cyber Hut online and in-person identity and access management training courses: Authentication Design & Management.
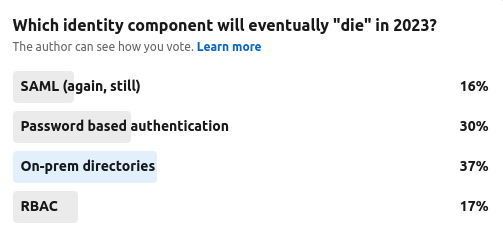
Each year a particular standard, component, model or approach within the identity and access management will be declared "dead" by expert commentators, startup vendors or just the bloke in the pub. As part of The Cyber Hut's Tuesday polls, I decided to test the water on this highly emotive topic before the Christmas holidays for our last poll of 2022.