Enjoy free weekly industry analysis and comment.
Join hosts Simon Moffatt and David Mahdi on The Week in Identity podcast – where they dive into the world of identity, cyber, risk and data security – and provide independent industry analysis and insight.
Modular and Flexible Industry Analysis and Research
We pride ourselves on delivering a zero-to-hero approach to industry enablement – from foundational training, contemporary curated headlines and commentary and detailed buyer support and research.
IAM Bitesize
Key IAM and identity-security terms and concepts in 10 mins or less
Most recent topic free
Acronyms and concepts
Broad array of topics suitable for industry and consultancy
IAM Radar
Industry tracker and analyst comment covering 100+ IAM vendors
Most recent article free
News, product updates, funding
Expert analyst comment and curated headlines on contemporary news
IAM Buyer
Detailed reports and market guides for a range of emerging IAM sectors
Market cheat sheets free
RFP support and questions for vendors
Capabilities and use case descriptions and architecture design
Latest Self-Paced Training ->
Learn how to design, build and assess secure and usable login experiences for B2E, B2C and IoT based ecosystems. Over 7 hours of recorded content.
authentication design and management
Latest Free Insight ->
The IAM Vendor Tracking Radar
The Identity and Access Management IAM Radar provides continual vendor tracking, with curated headlines and expert analyst comment across a range of both established and emerging vendors. Events as they happen, mapped to human intelligence.
The Week in Identity Podcast
The Cyber Hut runs a weekly podcast – aptly named “The Week in Identity” – where we take an industry analyst view of the latest identity and access management events, funding and conference news. A weekly independent briefing to provide buy side insight.
IAM 2 Industry Analysis Map
The Cyber Hut tracks a range of vendors in the global identity and access management space – from established platforms, through to emerging startups focused on niche use cases. We call this IAM 2 – the Identity and Access Management Industry Analysis Map.
Trusted by Global Vendors, Integrators and Industry
The Cyber Hut has supported a range of vendor, buy side, integrator and investment clients to enhance their content, understanding and insight on the emerging identity and access management markets – through training, advisory, content and inquiry.





















We Will Help Improve Your:
Industry Knowledge
Track emerging and established identity and access management vendors and understand their capabilities and strengths.
Security Posture
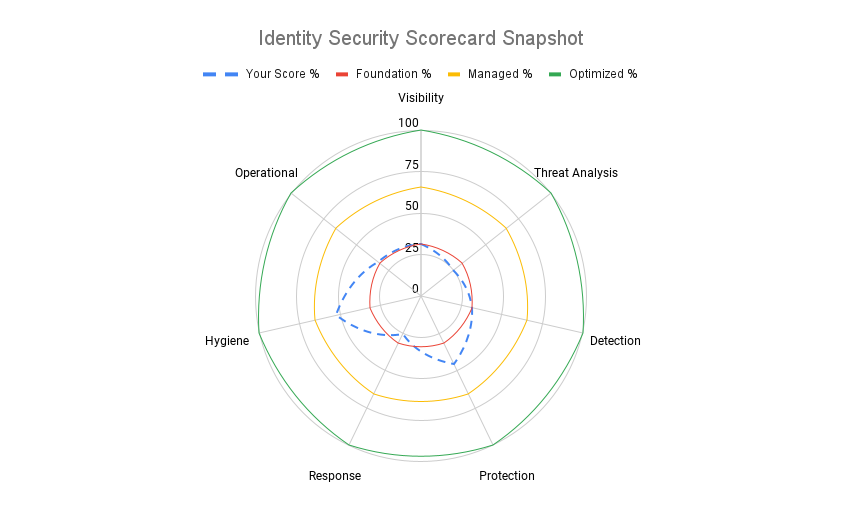
Leverage an Identity Threat Assessment Framework to help reduce risk, improve security and optimize existing IAM technology.
Maturity Awareness
Leverage independent opinion to compare to existing vendors or industry peers to help road map future IAM design decisions.