Next week our founder Simon Moffatt will be speaking at an event in London with leading customer identity and access management platform provider Transmit Security.
The event is entitled “The Fusion of Identity Management and Fraud Prevention” and will take place on May 23rd at One Great George Street, London. The day long gathering will contain an array of guest talks from industry leaders, practitioners and consultants, discussing the rise of fraud within the identity life cycle – from account on-boarding and proofing through to deepfake authentication techniques.

Simon will be delivering a keynote on the convergence of IAM and fraud and discuss the back story to both sectors, before discussing some important attack patterns being observed within our identity infrastructure. But what does a converged IAM, fraud and cyber landscape look like and how can organisations get there?

As most successful digital programmes are now major targets for fraud activity, organisations looking to deliver customer, citizen and consumer focused identity services, must now consider how they will integrate fraud detection and management capabilities at all parts of the identity life cycle. Isolated verification services and a lack visibility across the post-login activity touch points has opened avenues for malicious activity that ultimately results in lost revenue, degradation in trust and data quality issues.

Registration for event is available here
NB – updated 24 May with retrospective:

Key takeaways post event:
- Fraud is occurring at all parts of the identity life cycle – from on-boarding and proofing, through to authentication, credential reset and transaction processing
- Point in time identity verification solutions have become too isolated – and are not typically linked to digital authentication events
- Typical attack patterns are leveraging deep fakes during on-boarding, and also the use of harvested and fake data to create both blended and synthetic identities with credential harvesting and social engineering being used to breach authentication systems
- Basic rule based systems (IP, user-agent, geo-location) can help, but require substantial additions via automation and monitoring
- Bot protection at the earliest part of the identity interaction essential
- Identity is becoming a data problem – from login and context capture, through to threat intelligence, activity and other signals – but this requires strict integration and monitoring – too many occasions this data will not be collated or aggregated
- Fraud requires components across many parts of the identity and event life cycle – to detect, manage a response and remediate – with prescriptive feedback into permissions, login and usability systems
- AI is here to stay – and whilst an asymmetric advantage may exist in the short term for the adversary, the longer term benefits should empower blue team defenders
- Resilience across all parts of the identity life cycle are required to not only combat fraud and cyber criminal activity, but to deliver robust customer experiences
- Modern authentication techniques (such as passkeys) need to be delivered in a consistent, consolidatory way that has a broad application coverage
- Standards such as eIDAS will eventually bring benefits to both the end user (via selective data sharing and control) as well as public and private sector service providers (via fraud reduction and improved identity assurance) – however care must be taken with respect to empowering and educating the end user with the use of concepts such a wallets and data protection.
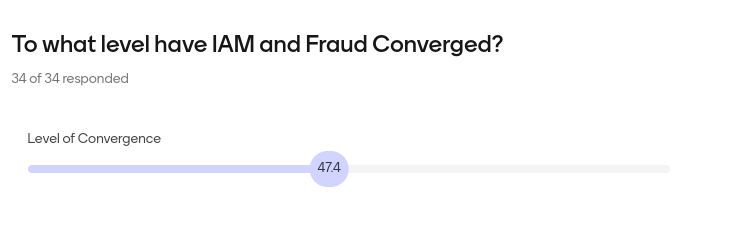
A live poll conducted during Simon’s talk asked the question to what level have fraud and IAM converged – 34 responded with the following average percentage: