Research Reports
Detailed standalone research
We provide a range of standalone independent research reports that are used as part of market intelligence, due diligence and procurement advisory.
From executive summary vendor assessments through to virtual proof of concept technology test drives, our reports are available on a pay as you go and vendor reprint basis.
Continual Vendor Tracking
Daily and monthly comment
Our
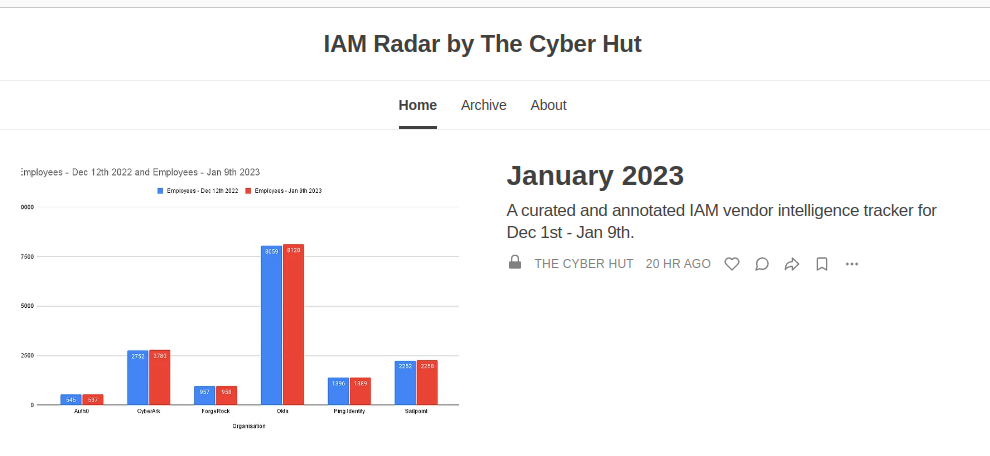
IAM Radar provides continual intelligence, insight and expert analyst comment on a range of established and emerging vendors in the global identity space.
We track a range of open source intelligence signals to create a curated headlines and comment service.
1 – iam radar
Market understanding
Continual industry comment across a range of established vendors – using a curated list of their social narrative, product news, case studies, funding and events.
2 – vendor assessment
executive summary
Leverage a high level executive research report on a selected vendor – using open source intelligence, vendor briefings and desk based research.
3 – technology test drive
virtual proof of concept
A detailed long read product labs report performed as a virtual proof of concept. Software usage, implementation and step by step screen shots and comment.
Latest IAM Vendor Insight
Comment and analysis on established and emerging vendors in the global identity and access management space.
Passwordless authentication is often described as improving both the usability and security aspects of both the employee and customer identity journeys. Many approaches to passwordless have emerged over the last 5 years - including hardware, software, biometric and standards based initiatives.
In November 2021, The Cyber Hut released a 61 page buyer guide for passwordless authentication, describing the vendor capabilities, requirements, integration options, B2E and B2C use cases and planning recommendations for migration.
A brief snapshot of questions to consider, when engaging software based solution providers in this space is described here.