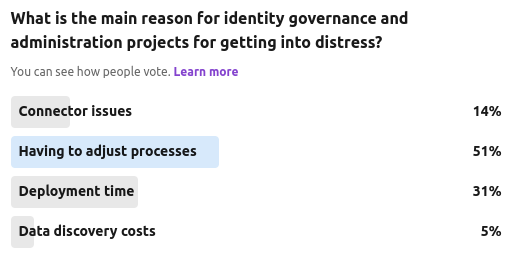
A discussion on modern identity governance and administration requirements and why many projects are in distress.
Our latest community poll was focused on the ever growing murmur that many privileged access management (PAM) and identity governance and administration (IGA) capabilities are either starting to overlap, or dedicated solution providers from each world are starting to add in "lite" functions from each others feature set.
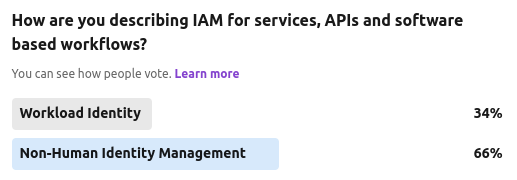
We ran another anecdotal community poll recently, asking whether this area of service IAM should be termed as "workload identity" or the more emerging "non-human identity".
The Cyber Hut recently ran a 7 day community poll on LinkedIn asking which of four big-ticket items will organisations be looking at from an identity and access management point of view.
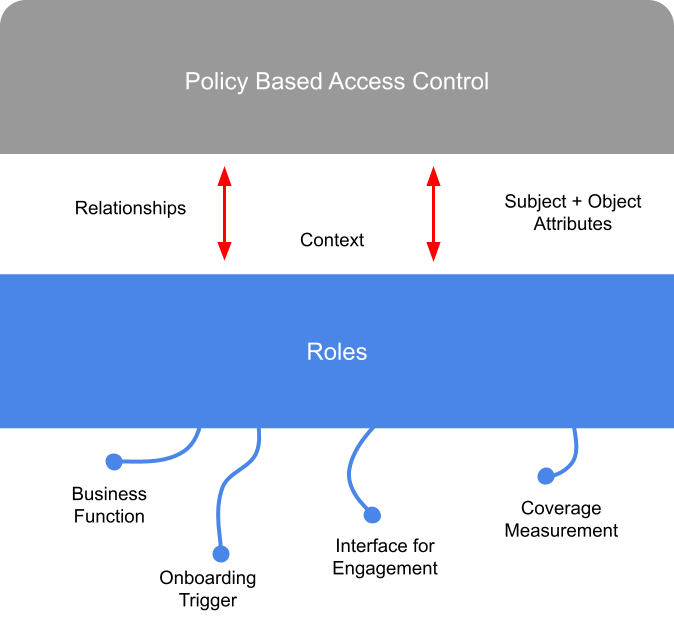
A discussion on how role based access control may still deliver business value, if deployed in a slightly different way.
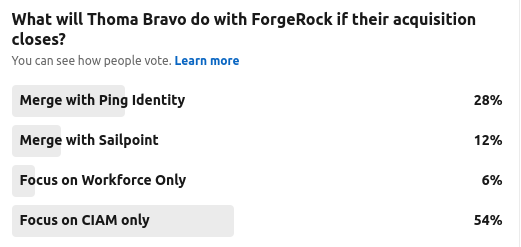
An opinion piece analysing the potential acquisition of ForgeRock by private equity firm Thoma Bravo.
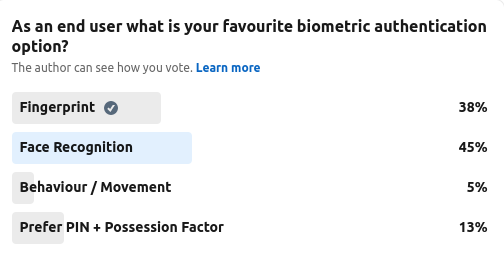
As part of The Cyber Hut's anecdotal community polls, we asked as an end user, what is your favourite biometric authentication option? The rise of device specific biometry to unlock our Android and iPhone based devices has increased in the last 3 years and many smart phone users will chose this over a basic PIN (albeit PIN is likely still needed after a hard reset).
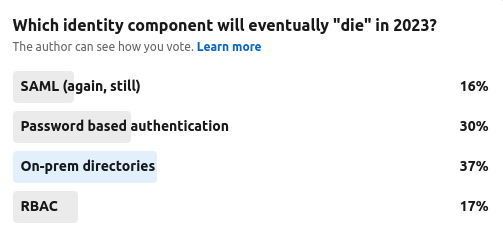
Each year a particular standard, component, model or approach within the identity and access management will be declared "dead" by expert commentators, startup vendors or just the bloke in the pub. As part of The Cyber Hut's Tuesday polls, I decided to test the water on this highly emotive topic before the Christmas holidays for our last poll of 2022.
Two weeks ago we ran another of our LinkedIn polls, querying the cyber, identity and access management community around a perennial question the industry has yet to consistently provide an answer for - in both user behaviour and technical solutions - "would you pay for privacy?".
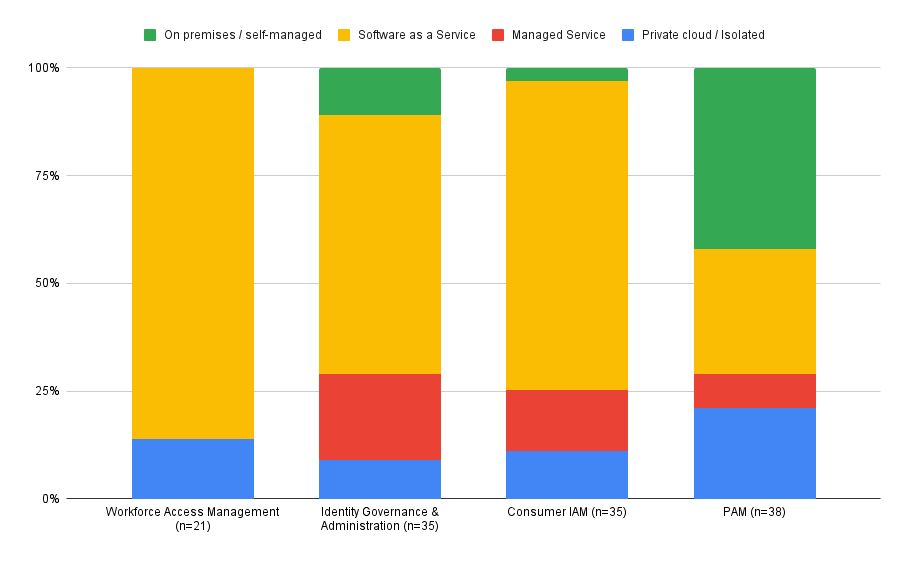
Over a 4 week period I asked the preferred deployment model option for four key identity and access management services: consumer identity, workforce access management, identity governance and administration and privileged access management.
The results where subtle and nuanced.