Passwordless authentication is often described as improving both the usability and security aspects of both the employee and customer identity journeys. Many approaches to passwordless have emerged over the last 5 years - including hardware, software, biometric and standards based initiatives.
In November 2021, The Cyber Hut released a 61 page buyer guide for passwordless authentication, describing the vendor capabilities, requirements, integration options, B2E and B2C use cases and planning recommendations for migration.
A brief snapshot of questions to consider, when engaging software based solution providers in this space is described here.
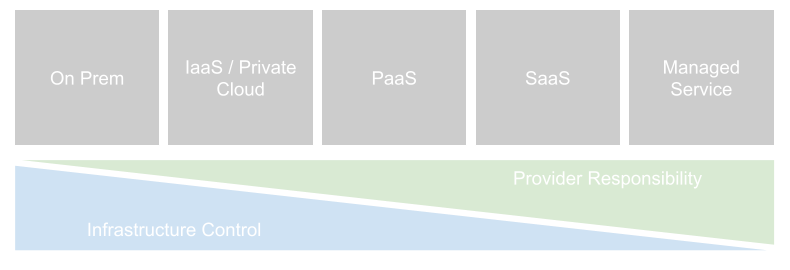
Even as many organisations are moving to a "cloud first" strategy for the consumption of new applications and services, the cloud line is blurred. Not all services can be consumed in a pure cloud setting, and not all "clouds" are the same.
Any analysis in the popularity, options or strategy with respect to IAM deployment should be firmly based against a set of basic definitions.
Join our founder Simon Moffatt on September 15th where he will join PlainID on a discussion around external authorization platforms.
The modern digital native enterprise is facing a number of emerging and incumbent challenges - from increased competition and demand for a more agile service deployment model through to needing the ability to share more data to more people, all under a competing climate of increased security threats coupled with a lower risk appetite.