Identity and Access Managements systems have gone through a significant transition over the past 7 years or so with respect to how those systems are being deployed. Clearly IAM is broad and varied ranging from B2E workforce access management, privileged access management and consumer/customer/citizen identity and access management through to identity governance and administration as just a few mature areas.
Even as many organisations are moving to a “cloud first” strategy for the consumption of new applications and services, the cloud line is blurred. Not all services can be consumed in a pure cloud setting, and not all “clouds” are the same.
Any analysis in the popularity, options or strategy with respect to IAM deployment should be firmly based against a set of basic definitions.
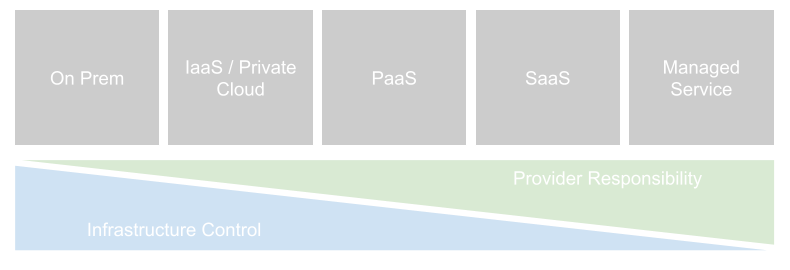
The above image tries to capture the main models. The sliding responsibility bar at the bottom show the changing levels of responsibility and control, split between consumer and provider. The concept of a “cloud shared responsibility” model is not new. Most cloud service providers (CSPs) have them (see AWS here and Microsoft here for example). An agnostic description is provided by the UK’s National Cyber Security Centre and is available here.
The main idea, is to describe who (the cloud consumer or the CSP) is responsible for each part of the functionality.
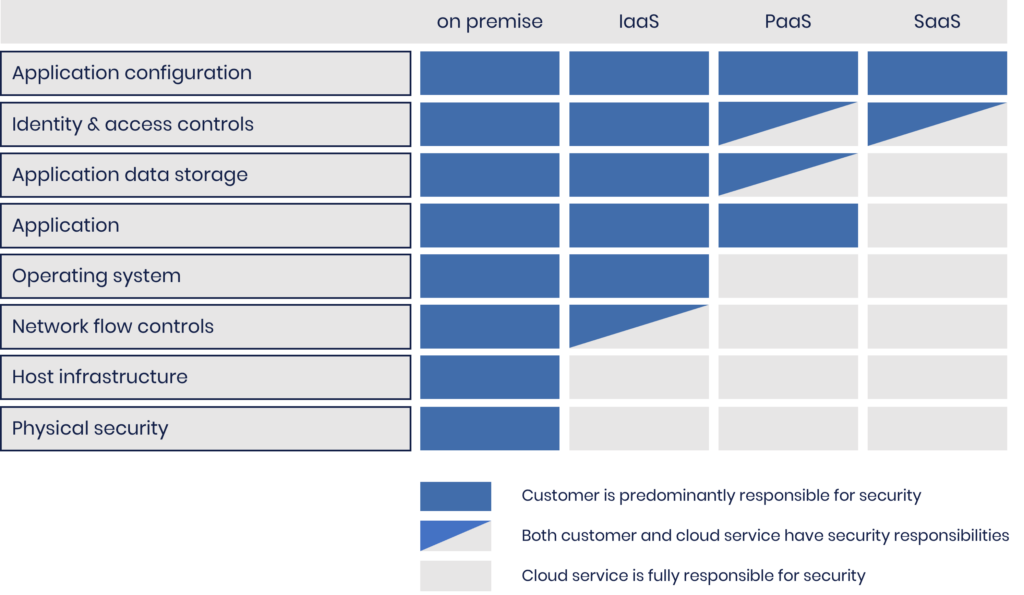
Let us take a look at each deployment bucket in turn and may in both the what and the why and some example suppliers.
On Premises
| The What | The use of client controlled hardware, virtualisation or container technology to deploy binary based IAM services |
| The Why | A requirement to integrate with upstream (data sources) or downstream (applications being protected) systems that can not be migrated away from fully controlled ecosystems, perhaps due to compliance. |
| Prerequisites | Dedicated infrastructure personnel (network, virtualization, server, container, web technologies); identity and access management operational support; identity and access management design/consultancy. |
| Benefits | Full control and ability to customize deployment and perhaps entire software stack. |
| Costs | Run operate costs. Specialist personnel. External consultancy. Long term investment. |
IaaS – Infrastructure as a Service / Private Cloud
| The What | Outsourcing of core infrastructure and computing power to a third party. The definition of a “private cloud” is generated by leveraging a cloud provider for compute power which delivers cloud capabilities (volume, scale, elasticity) but with isolation with client controlled deployment of APIs and services. |
| The Why | Identity is complex and many projects require customization for data integration and usability. The ability to still control deployment, yet outsource the costly infrastructure aspects provides a variable compromise of operation liability and deployment flexibility. |
| Prerequisites | Selection of a CSP and strong knowledge of how to manage and deploy core compute, storage or container infrastructure. |
| Benefits | Control over the deployment model, customization of core software APIs and user interface. Isolation away from “noisy neighbours”. |
| Costs | Specialist cloud service provider API knowledge as well as identity customization skills. Likely reliance on system integrations and external specialists. |
PaaS – Platform as a Service
| The What | An outsourced platform, where not only the infrastructure and compute power is delivered by a third party, but the core identity components and APIs are outsourced too. Application integration and some level of core API customization is possible. The delivery model may well be single tenant – that is per-client isolation of deployment. |
| The Why | Identity services are middleware – enablers to other technology goals – and customization is often required either for data or application coverage. A platform of wide ranging features allows the client to deliver complex services without investing in infrastructure. Typically used by larger enterprises with broad requirements. |
| Prerequisites | Specialist identity design, integration and operational support personnel – either in-house or via external specialists. |
| Benefits | The delivery of complex identity platforms – either for large workforce or external consumer communities – without the need to invest in the run and operate mechanics. |
| Costs | Large subscription costs due to the outsourcing of both infrastructure and a broad array of identity capabilities. Specialist personnel to integrate against the platform in order to leverage a RoI and not result in “shelfware” and unused APIs. |
SaaS – Software as a Service
| The What | Software as a Service is often seen as the main and only “cloud” identity offering. In this case the entire service and API is delivered by a third party – albeit the main difference to a PaaS, is the number of use cases covered is likely to be considerably smaller. The delivery model is likely multi-tenant too. |
| The Why | The client requires a subscription based, entirely outsourced delivery of a service or API. PAYG pricing, rapid startup and limited use cases, allow for a simple to use and operate service. |
| Prerequisites | A SaaS reduces the number of technical requirements – fewer specialists are needed to run and operate and due to the simplicity of delivery, integration steps are normally simple and less of them. Operators of the service are likely to be non-technical. |
| Benefits | Entirely outsourced, which is simple to engage with, start and more importantly exit from. Metrics and dashboarding are likely to be of a good standard, allowing success criteria to be monitored and distributed to non-technical stakeholders. |
| Costs | Pricing is typically on a per month or per year basis – and whilst startup costs and effort may be small, longer term use cases may not be easily fulfilled, as the SaaS supplier has a broad array of customers to service and may not be well suited to highly customized use cases. |
Managed Service
| The What | An entirely outsourced model, where both the infrastructure, platform and personnel used for integration, operations and management are derived from a third party. |
| The Why | Many organisations both small and large, do not have the specialist personnel needed to design and operate an identity platform. However, SaaS services may not be able to cover more complex use cases or have the ability to consistently integrate against on-premises, complex or legacy systems. |
| Prerequisites | Managed services may be costly in both a time and finance point of view due to the infrastructure and personnel costs. The managed service will also likely require some design effort up front in order to deliver the correct level of customization. |
| Benefits | A highly customized service, that has the benefits of economies of scale and specialist provider skills. Allows an organisation to receive both the service as well as metrics, measurement and continual redesign / evolution. |
| Costs | Likely to be a large monetary cost as well as some design effort up front in order to derive the long term benefits. |
