A few weeks ago I ran a slightly provocative and not very scientific poll on LinkedIn asking which was the more important: authentication or authorization? Clearly in the grand scheme of things that is a pretty pointless exercise, but the rationale was to really identify some thought processes and reactions. It provided some interesting responses.
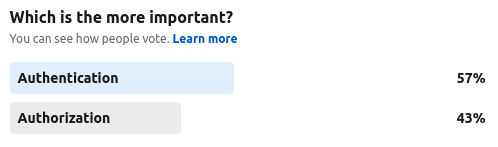
Some Numbers
- Authentication received 57% of the votes
- Authorization received 43% of the votes
- The poll lasted 2 weeks
- Overall 191 people voted
- The post was viewed over 17,000 times
- The post received 23 reactions and 48 comments
Should Authentication Have Won By More?
So what does this really mean? My expectation before the poll was that authentication would take a must larger percentage of the vote – perhaps closer to 70%. Authentication – working out who someone or something is, via an assertion – is really the pinch point to most website, application and service interactions. There are very few interactions that occur under a truly anonymous pattern. Most systems simply require you to login – be it with a simple email and password, or with an additional multi factor authentication option or even passwordless. The market for authentication technology is also large and mature – and also growing. A basic Crunchbase query reveals that nearly $3 billion of funding has been sunk into organisations with an authentication function since January 2018. That doesn’t include the pretty spectacular $543 million that Transmit Security received in June.
Authorization on the other hand is a more complex beast – often seen as specialist, complicated and only really leveraged for the most important of systems. 15 years ago I spent several years in the role based access control (RBAC) space helping to architecture role mining and identity certification systems. RBAC was seen as the saviour for employee authorization. It ended up being a costly and binding approach, with many organisations facing months of expensive consultancy and fairly rigid and unresponsive authorization systems. Is that still the case today?
Can Authorization Work Without Authentication?
Well in honesty it probably can’t. The authorization paradigm typically needs a few components in order to operate: an identity (or subject), a resource, some actions and some environmental context. So this typically translates to authorization questions like “Can John Doe read the file addressbook.csv on his laptop, on Monday at 5pm”?. A centralised policy decision point will take that question, analyse a set of pre-configured policies and look to send back either a yes or no style response, or perhaps details about what “John Doe” can actually do, to what and when. By association for that style of querying to work, we need the subject aspect – a value typically personified by things like cookies, session objects or OpenID Connect id_tokens. To get any of those you need to authenticate… Of course there are some other more obtuse authorization models, perhaps relying purely on time, task or behaviour based characteristics that are not entirely relying upon a subject. We’ll put those to one side for now. Without authentication, authorization can be relatively ineffective in the typical web, application and API environments.
Is Authorization Hitting the Big Time Again?
There have always been dedicated and specialist authorization providers – either as part of an overall identity and access management platform or as standalone and integrated components. Are they now on the rise again? Concepts such as zero trust network architecture, data centric security and continuous adaptive risk and threat assessment, all place identity at the centre of the security landscape. But does that mean? It means the subject aspect of those authorization decisions is becoming more critical.
We’re starting to see two distinct patterns emerge: greater emphasis on binding the authentication to greater levels of biometric assurance and more flexibility when it comes to post authentication events. Authentication doesn’t exist in isolation or a vacuum. End users authenticate in order to do something. Go to work. Buy a book. Read a news article. Transfer money. Order a taxi. The “what happens” next aspect is becoming more varied and more distributed. The authorization aspect is suddenly thrust front and centre of the “post authentication” landscape. Who can do what, when and where now needs to apply to single page apps, microservices, IoT interactions, consumer identity life cycles, PII protection, intellectual property data access and more.
The last 18 months have seen a slew of dedicated authorization providers starting to hit the headlines, either with funding, new features or new launches including the likes of Scaled Access, Authomize, oso, Open Policy Agent, PlainID, Cloudentity, Opal and Aserto. Is authorization about to hit the big time again? With a healthy 43% of a totally unscientific poll, perhaps so.
Some of the comments on the original LinkedIn poll make for some interesting reading. I’ve left them anonymous…go back to the post to add your own thoughts.
- “Wow! It’s like asking, do you prefer the right side or the left side of your brain?”
- “Right Twix or Left Twix”
- “Now all seriousness, I think we have way more good solutions for authentication than we have for authorization. Both are extremely important, however authorization is less represented in general”
- “One thing is for sure: if any organization even remotely thinks about ZT or CARTA, they *need* the identity context for authorization”
- “Would be interesting to have compared this with a vote 5 years ago. I bet it would’ve been AuthN 90% and AuthZ 10%. Then this poll would show what we see happening: an increase in awareness around the necessity of an Authorization strategy.”
- “Authorization is usually harder.”
- “Just because I know who my kids are, doesn’t mean they can get cookies from the cookie jar! At least not until I say ✅”
- “Zero Trust Overlay Networks is the way forward. Authenticate first and only then connect.”
- “You can have access without authentication. Not a lot, but you can. Guest access is a very limited authorization. And in ZTA you can even have access without an account, services just need to rely on a trusted Identity Provider. And matching authorizations.”
- “What’s the use of authentication without authorization?”
About The Author

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. He is also a part-time postgraduate on the GCHQ certified MSc. Information Security at Royal Holloway University, UK. His 2021 research diary focuses upon “How To Kill The Password”, “Next Generation Authorization Technology” and “How IAM Countermeasures Can Defend Against Cyberwar”. For further information see here.
The Cyber Hut can provide a range of vendor independent authentication and authorization architecture review services. See here for further details.
