In Their Own Words
What Is Nullafi
“We’re an award-winning SaaS cybersecurity company with multiple patents granted for our data aliasing technology. The goal of our company was to set a new cybersecurity standard. While traditional methods all clamor for incremental improvements and competitive advantages in breach prevention, we stand apart (and “are notable” as Forbes puts it) for our different approach: we nullify the breach, aka, make it simply not have any impact on your company.”Our Mission
“In short, make data breaches not matter. Our core belief is that data security should be made as easily achievable as possible for organizations who care, and that the data security landscape is filled with complexity, cost, and lack of results. Our mission is to create data security tools that are: Easy to Use, Affordable, Flexible and Scalable”.It’s Time For Something Different
“Breaches are inevitable. With Nullafi, it doesn’t matter – your data is literally useless to cybercriminals.Nullafi provides smarter, simpler data security, so even if hackers get into your data, or your data is lost through other means, you remain insulated. The cybersecurity world has focused too long on trying to stop data exposures by simply shoring up perimeter defenses. In a perimeterless world with a constantly evolving threat landscape, it’s no wonder this unifaceted approach keeps failing.
Nullafi’s proprietary data aliasing protocols offer a breakthrough in security, with flexible integration options that dramatically reduce risk, and don’t just shift it. According to Perkins Coie, our customers avoid 97% of the financial fallout of a data breach, and can continue their business operations as normal.” –
nullafi.com
Key Facts
| Links | LinkedIn: https://www.linkedin.com/company/nullafi Web: https://www.nullafi.com/ Twitter: https://twitter.com/nullafi |
| Founded | 2014 |
| Founders | Andreas Imthurn, Elder Santos, Robert Yoskowitz, Stephen Yoskowitz |
| Funding | Seed in April 2016 |
| Number of Employees | < 20 |
| HQ | Chicago, USA |
What Do They Do?
Nullafi are a data centric security platform. They essentially allow fine grained controls to be applied to individual data fields within third party repositories. They provide an endpoint agent that sits on the controlled laptop of an employee, which in turn integrates with the Nullafi cloud service. The combination of data policies in the cloud control plane and the endpoint agent, allow individual data fields to be removed, masked or redacted before the data reaches the user’s laptop.
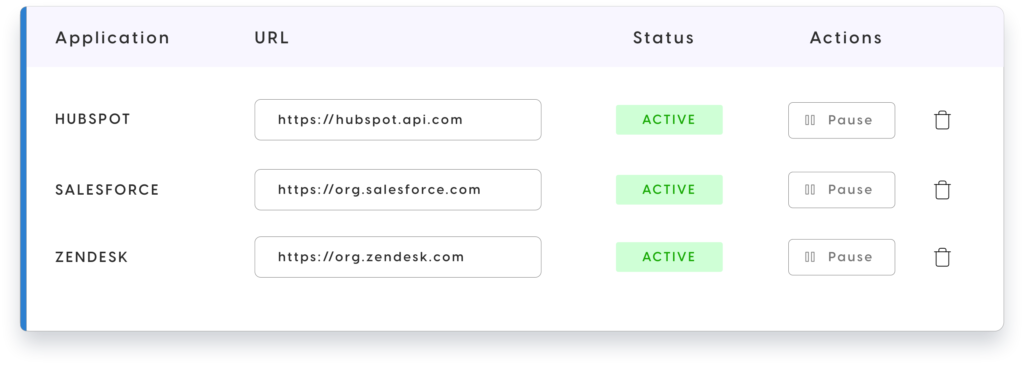
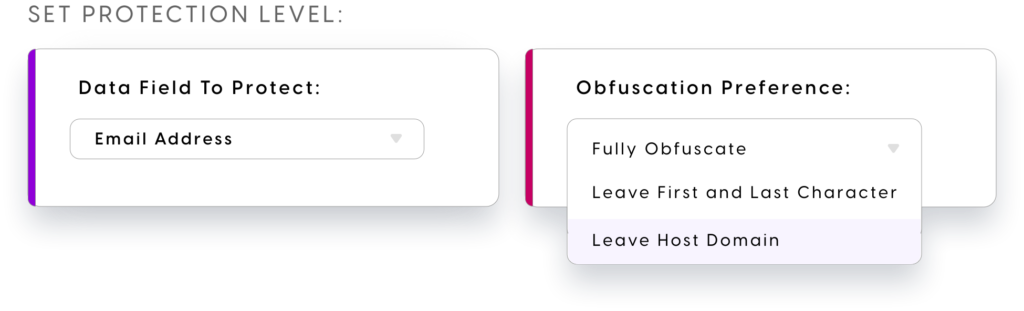
Policies are associated to individual service applications, with the necessary service specific schema. Each field can then have specific rules attached to them, which trigger based on specific conditions.
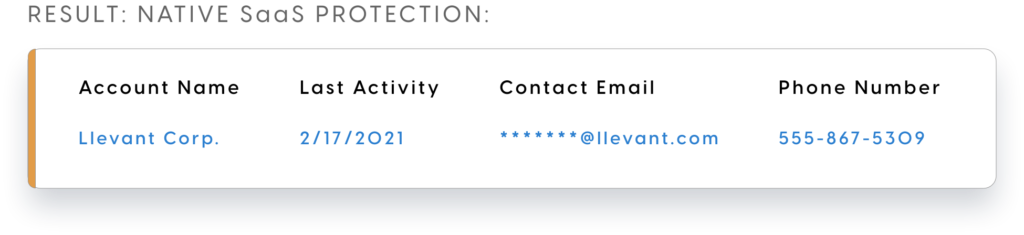
Rules development and deployment is aimed at the “no code” narrative, with simplicity and speed to control mentioned on numerous occasions. Out of the box service integrations are mentioned for Salesforce, Hubspot and Redash – all common platforms where data is often very sensitive. Think contact details, credit cards and so on.
Nullafi are seemingly providing two components a “Shield” and “Vault/SDK” option. The Shield seems to comprise of both an end point agent and a cloud control pane. Data from the protected service seems to go via the Nullafi proxy API, where the necessary rules are processed. The data payload with the necessary redactions and edits in place, is then forwarded down to the end device via the agent. This is providing more than just a client side data masking function, but more an end to end data management security solution, with the masking occurring before the payload from the third party arrives at the endpoint.
They leverage the POLP (principle of least privilege) argument, to limit who can see certain protected data fields. The service integration piece, is based on a URL. Traffic heading to the data source URL, is intercepted by the end point agent and in turn interacts with the Nullafi proxy API, to determine which fields to control and under what conditions. The rule definition is seemingly only focused on identity provider data such as groups to identify who the rule should apply to.
As traffic routes through the Nullafi proxy API, they have the ability to create an “activity tracking” function, which essentially records the who, what, where and when with respect to data access.
The Vault/SDK approach seems more aimed at custom data sources and provides an end to end data alias and vaulting service, that protects data client side before using data field replacement alias’ managed via a secure API fronted vault.
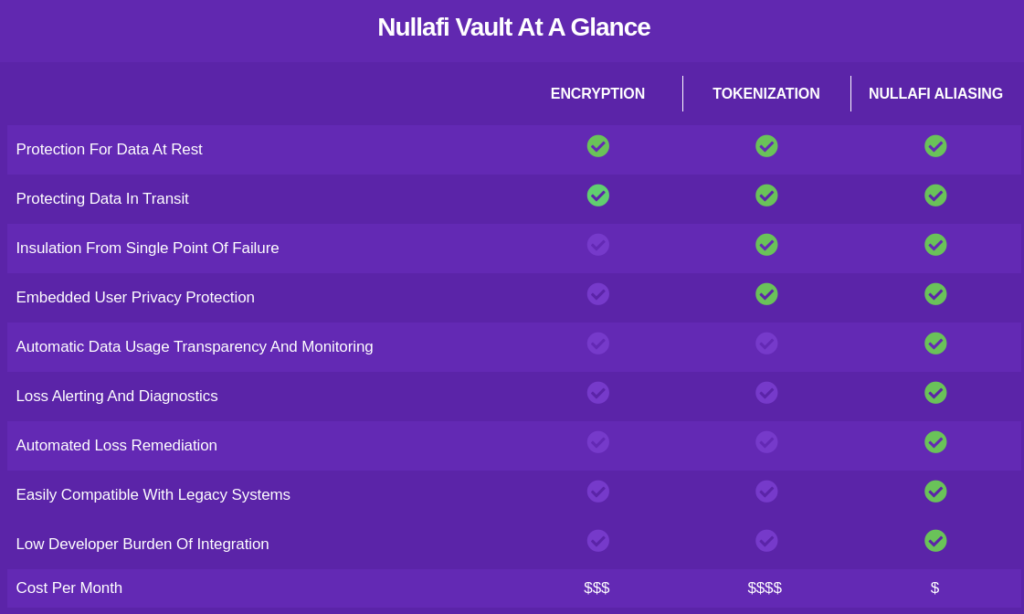
Why Is This Important?
Organisations are trying to move towards zero trust network architectures – where transaction trust is moving from location details such as IP addresses, to a more trust-but-verify model based on the user identity and device. Nullafi take the identity approach and overlay with data centricity. Hackers want data. Data breaches are based on data. In this model, Nullafi push the control plane right down to not only the data, but to specific fields within the data.
Why Is It Interesting Now?
Data breaches are at an all time high, but protection tooling is often attacking the wrong problem. By creating protection functions within the information asset itself, helps to collapse the gap, that often occurs between authentication and authorization and downstream resource access time – the so called time-of-check to time-of-use (TOCTOU) process.
Why Are Nullafi Different?
They are not the first data centric protection vendor. See the likes of Immuta, Varonis or even the likes of the modern DB firewall and gateway tools like Acra from Cossack Labs. However, there are a few things that standout. Firstly the ability to be quite granular on the fields being protected and secondly the deployment model seems very simple. The focus of the Shield feature set to take a look at protecting third party cloud SaaS data such as Salesforce and HubSpot is also interesting.
