Recently I discussed how “You’re Only As Strong As Your Password Reset” – with an emphasis on how credential reset activities could well be an Achilles heel when it comes to authentication journeys. Whilst many organisations rightly start to add multi factor authentication and passwordless authentication to their arsenal of security and usability controls, it is important to also focus upon the related components of authentication, such as device migration and reset.
As part of the research I’m lucky to work on at The Cyber Hut, I’ve been involved since May on analysing the market for passwordless authentication. The culmination of this work will be the research report “How To Kill The Password: A Buyers Guide To Passwordless Technology“. One thing that has become clear, is that the vendors who are developing the most complete range of authentication options, tend to think about authentication holistically – and that authentication really has many different parts that contribute to a larger service goal.
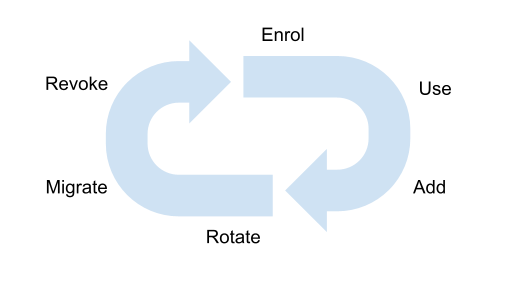
If we start to think about authentication, and especially authentication that is relying on device binding and biometrics, we have to start thinking how a credential is issued, why it’s issued and under what levels of assurance has it been issued.
Can the credential be extended and made available to other devices? Clearly a reset (or rotate) activity is also relevant especially when most passwordless technologies are heavily reliant on asymmetric cryptography. Does that rotation event require changes to relying parties, identity providers or downstream applications?
A common use case of mobile device based authentication is migration to a new device. Can that be done via self-service, perhaps via QR codes with interactions required on both the new and old devices? One stage I left out, is that of recovery. Many seem to handle this as a re-enrolment activity, mainly due to the lack of credible methods to store private keys away from a device. There are some vendors (Keyless.io springs to mind) that offers a distributed method of key storage, that perhaps makes recovery much easier. Are there any other stages that are missing? (Contact us if you think so).
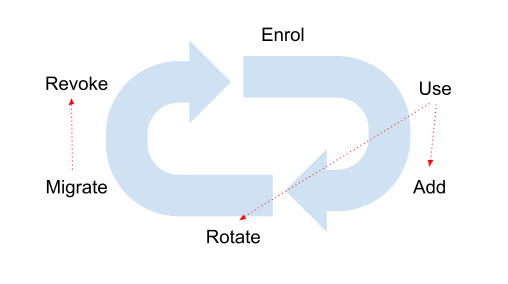
One thing is clear, that a credential life-cycle is not linear. Usage will clearly result in rotations for example. A migration should result in a revocation event for an existing device too. A lost device, essentially results in a rotation or reset.
Another interesting aspect, is that authentication is really a means to an end. The “use” stage on it’s own does not achieve a great deal. Read any decent book on cryptography that mentions “entity authentication” and the entity is really on their way to do something. Alice is sending a message to Bob. Bob is going to make a purchase. Alice is opening the door at work. The usage aspect is becoming increasingly important from an end user’s happiness perspective, especially if the authentication event exists in the consumer identity world.
The usage needs to be wrapped in privacy preservation, yet provide a level of assurance that proves that Alice is in fact “Alice Smith” from Louisana and not just “Alice”. A level of real time biometric “liveness”, mapped into a level of assured enrolment that can empower downstream services that deliver personalisation yet support privacy preservation and data security. That is quite an ask.

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. He is also a part-time postgraduate on the GCHQ certified MSc. Information Security at Royal Holloway University, UK. His 2021 research diary focuses upon “How To Kill The Password”, “Next Generation Authorization Technology” and “How IAM Countermeasures Can Defend Against Cyberwar”. For further information see here.
