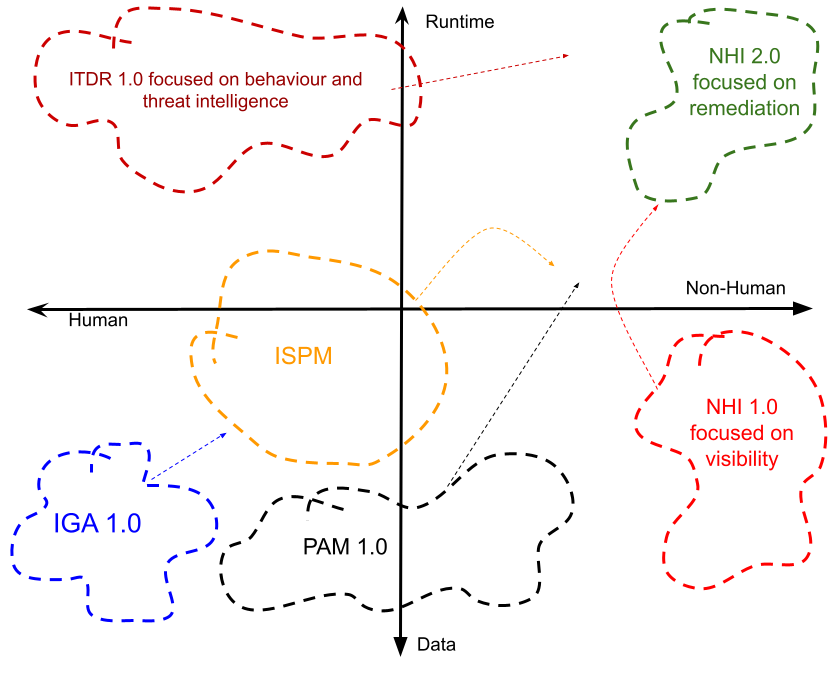
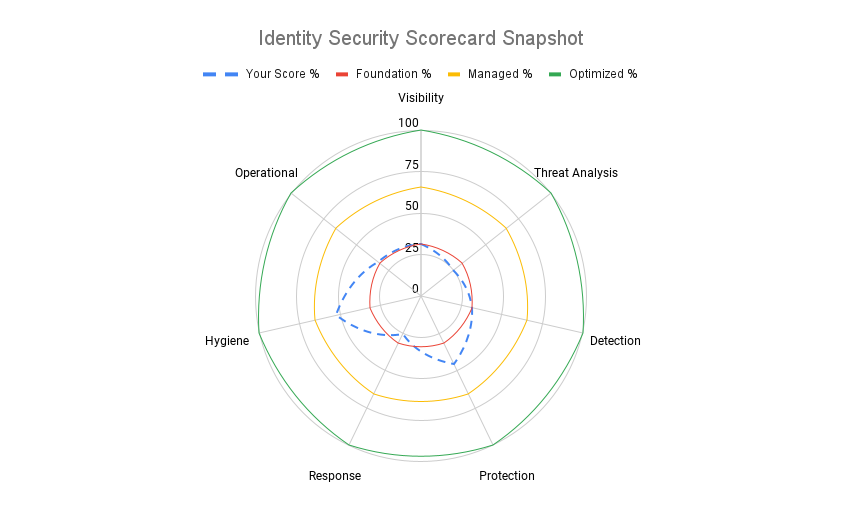
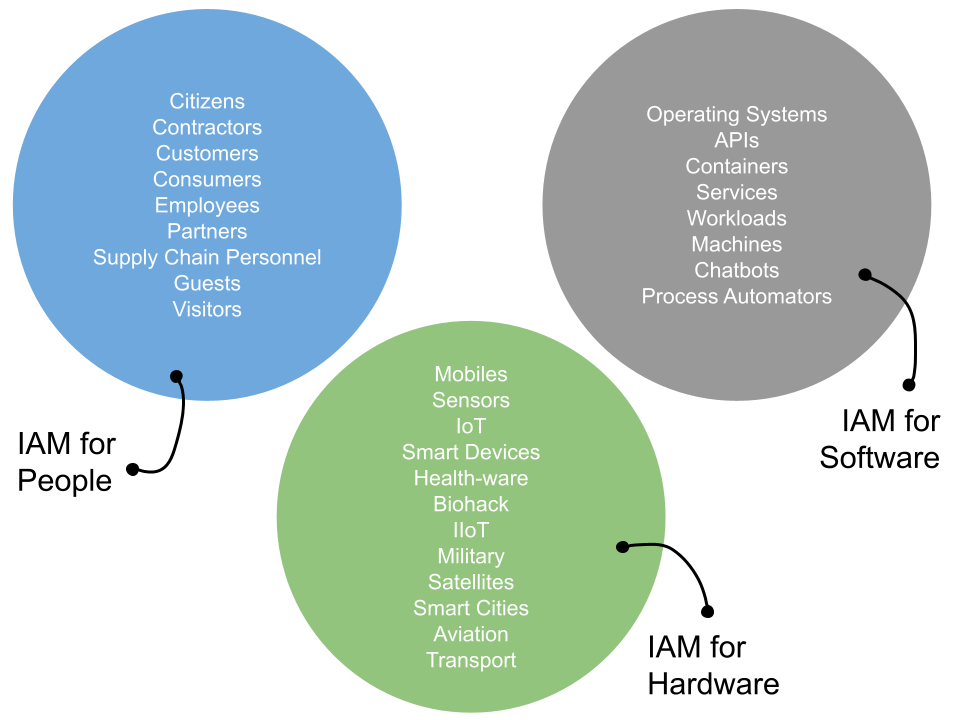
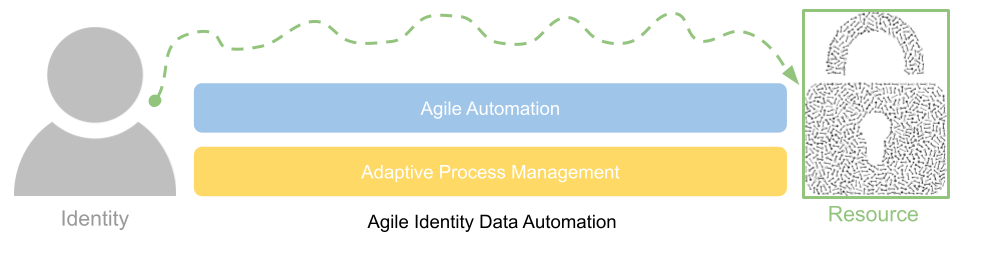
Identity Security is a topic we have tracked and discussed on numerous occasions at The Cyber […]
Our founder Simon Moffatt (a Fellow of CIISec) will be attending this years Chartered Institute of […]
Later in the month, our founder Simon Moffatt, will host a webinar panel discussing the rise of NIS2 - what it is, how it impacts identity and security controls and risk management and what pragmatic steps organisations can take to become compliant.
Our founder Simon Moffatt will be a panellist at the Think Digital Identity and Cyber Security […]
Identity Security – a complex, nuanced and yet equally dynamic, exciting and business enabling concept that […]
Later in month, our founder Simon Moffatt will be in conversation with Mickey Martin, VP Presales at PlainID, where they'll be chatting about the rise of identity-centric security and the critical role of authorization.
A discussion on the need to consider identity management as a set of life cycles - for expansion into the workload and NHI spaces.
Join our founder Simon Moffatt in our next industry webinar, where he will be in conversation with cloud identity governance and administration provider Omada on the concept of cloud IGA.
Identity Governance and Administration is now entering a new age – where the IGA problem statement has evolved, the opportunity to innovate and improve productivity are all around, yet many organizations are struggling with fragile and static on-premises IGA technologies built for yesterday’s problems.
A discussion on why existing IGA projects are often in distress and how a more agile data automation approach can streamline process and improve application connectivity.
Next week our founder Simon Moffatt will be speaking at event in London with leading customer identity and access management platform provider Transmit Security.
The event is entitled "The Fusion of Identity Management and Fraud Prevention" and will take place on May 23rd at One Great George Street London. The day long gathering will contain an array of guest talks from industry leaders, practitioners and consultants, discussing the rise of fraud within the identity life cycle - from account on-boarding and proofing through to deepfake authentication techniques.