Last month I ran a highly sophisticated and broad study of whether we need a new job role focused purely on Identity and Access Management. In actual fact it was just a LinkedIn poll, but as ever, these things provide a good coarse grained insight into some interesting problems.

So I had 84 responses, not a large number, but nearly all respondents worked in senior roles related to IAM – either as consultants, in-house or for vendors. So the opinions and responses where quite insightful.
Why Ask The Question?
Firstly why is this question interesting and worth asking in the first place? Well, identity has evolved and is no longer just the purview of internally focused IT operations, looking after the life cycle of employees and their single sign on and access request processes. “Identity at the centre”, “identity centric security” and other vendor strap lines, is seeing identity move somewhat out of a reactionary and internal focused function, into something more pervasive, broad and foundational. Identity services are now being used for:
- B2C – business to consumer – interactions with new use cases and requirements
- M2M – machine to machine and the application of non-person entity identifiers
- Service identifiers – this could fall under M2M but the likes of SPIFFE is on the rise
- IoT – the association of smart devices to a physical person and the transfer of scoped and time bound access
- RPA – process automation, including chat bots all need identities too…
- IIoT – the industrial world is absorbing some identity characteristics for tracking and data management
- B2B2X – complex supply chain, partner and mesh based infrastructures, sees identity relationships profilerate
- SSI – the decentralised nature of identity, may result in a non-B2C/B2E ownership model
The area that seems to be altering the organisational focus on identity is B2C – the consumer (or customer, or citizen) identity and access management (CIAM) area. Why so?
CIAM Alters the Identity Metrics
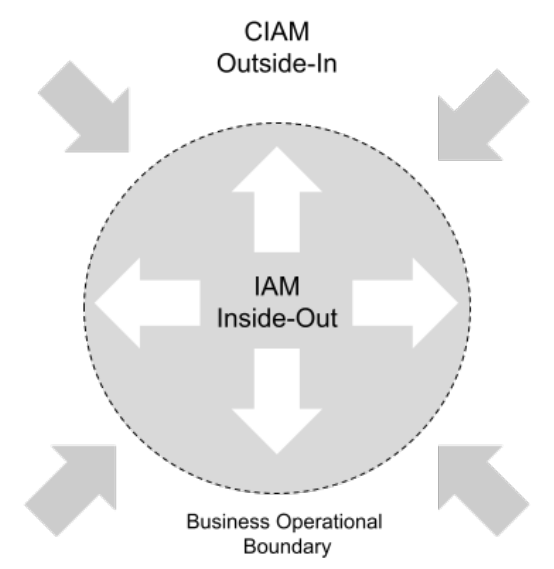
Obligatory sales plug, the above diagram is taken from chapter 1 of Consumer Identity & Access Management: Design Fundamentals where I compare B2E IAM and B2C IAM. So why is this interesting? Well CIAM is driving inbound relationships, based on different success metrics with different business stakeholders.
CIAM has some overlapping, but also some very different functional and non-functional requirements to B2E IAM. The budget holders and key interested parties are going to be very different. Here we need to think about the chief marketing officer (CMO) and potentially a chief digital officer (CDO) if present. CIAM is often described as being “user-centric” in its nature, whilst B2E IAM is “system-centric”, focused on automation and productivity advancement.
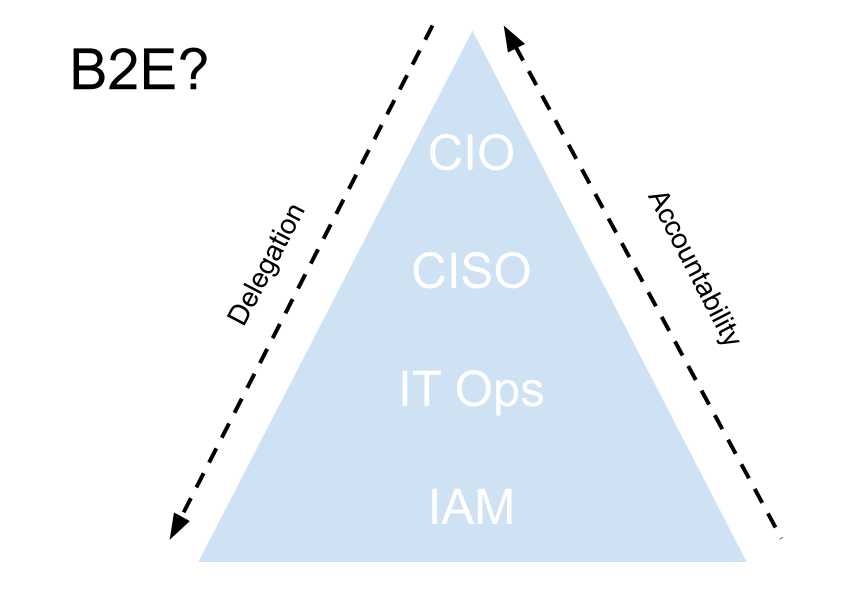
I wonder if we then start to think of B2E IAM as being inside the operating model of the organisation – reacting to business objectives and acting as a cost centre – in the sense it is not generating revenue, at best helping save money. The business hierarchy delegates authority and in turn metrics “down stream”. In this way of thinking the 39% in the above poll would be entirely correct. Do you really need to have an IAM process and metrics rep higher up the food chain? Probably not, in the same way you wouldn’t necessarily have a virtualisation point of contact or network perimeter representative.
But what if we just change the lens and think about the outside-in view of identity? What if we take B2C identity as the catalyst for business opportunity, empowering the organisation to deliver new services, engage new prospects and customers, deliver personalisation and be in a better position to react to external change and competitive pressure?
Here the metrics and accountability are unlikely to follow a B2E model.
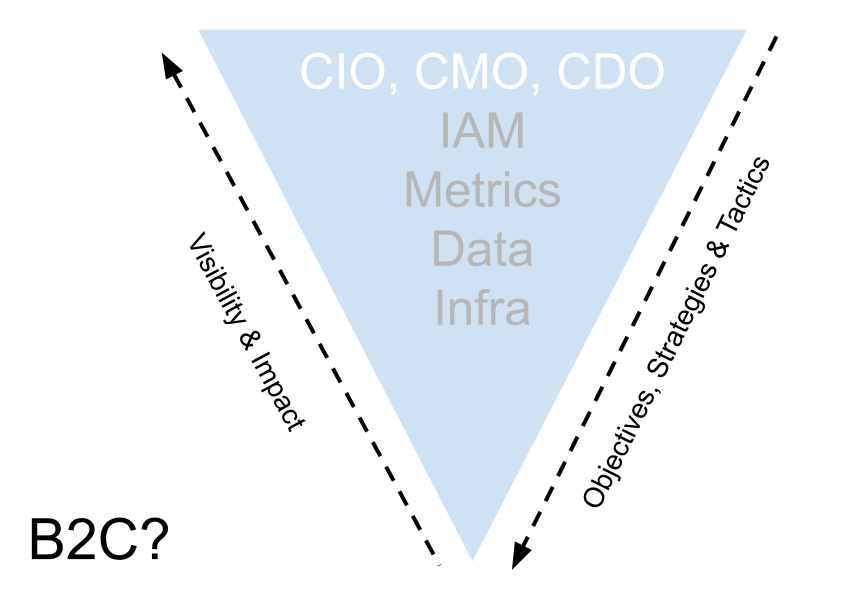
The above is just a quick sketch, and by no means empirical. But essentially the visibility of IAM increases, namely as the objectives of say the CMO become impacted by the B2C registration process or the metrics associated with abandoned shopping carts due to a poor MFA experience. The B2C IAM platform becomes more foundational, moving up the food chain to empower outbound facing business objectives – powered by infrastructure for data analysis and third party integration.
In this model would we need a “chief identity nerd”? Maybe not, but the C-level reps are doing to want to know more about the underlying functions that are powering things like registrations, personalisation, cross-sell or upsell-conversions and the like. Where does that information come from, can it be measured and who “owns” it?
Those questions may well be behind the 61% who see identity as being “too important” in the current operating models.
Some Quotes From the Poll
“Good question. Unfortunately, I don’t think most CISOs have a seat at the boardroom. An identity person reporting directly to CIO would make sense to me. Maybe the equivalent of an SVP but not necessarily EVP (depending on the org).”
“It could be a board level topic for sure, ESPECIALLY if you have customer facing offerings. Then board level makes sense. For traditional workforce, it needs to be a blend of UX surveys and security. Treat your employees like customers, especially as things move towards zero trust architectures and permanent WFH.”
“Like all good questions, I’ll answer this one with “it depends”! I don’t think it’s required in the majority of organisations, but I can certainly see where it may be required if identity is essential in meeting a strategic goal for a company – or in addressing persistent and changing threats. I’d also echo the comments about CISOs not having a seat, which effectively demotes identity (and security in general) further.”
“The CISO’s role is to explain all aspects of security (including IAM) to the Board. Adding in another reporting role will just result in more confusion within the Board, and not give you the result you think you’ll get.”
“Identity is the new perimeter – need a unique role to bring in the change with this new mindset all across functions of security, which is much more and beyond what a CISO can handle.”
About The Author

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. His 2022 research diary focuses upon “Next Generation Authorization Technology” and “Identity for The Hybrid Cloud”.
