This week saw the International Institute of Strategies Studies release a hefty 182 page report analysing nation state cyber security capabilities – from both an offensive and defensive point of view. The IISS also provided a launch video to introduce and discuss the report.
The report – a result of two years work – provided some interesting insights; not only on a new methodology on how to attempt to measure nation state capabilities, but also the results of the research and ranking of the various countries that were analysed.
Analysing nation state capability in cyber space is notoriously difficult. Many cyber capabilities – especially on the offensive side – are often not publicly disclosed for obvious reasons. Retrospective attack analysis, as well as the analysis of publicly available unclassified documents pertaining both to cyber strategy and funding, and also military strategy and foreign policy are needed in order to stitch together an assumed cyber programme. But all of this relatively qualitative and subjective of course.
The report created a methodology based 7 key components:
- Strategy and doctrine
- Governance, command and control
- Core cyber-intelligence capability
- Cyber empowerment and dependence
- Cyber security and resilience
- Global leadership in cyberspace affairs
- Offensive cyber capability
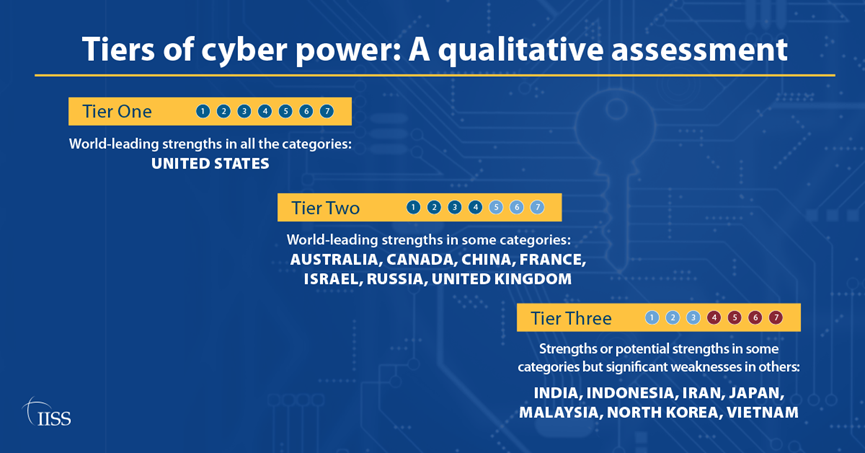
A host of nations including the Russia, China, the “five eyes” – including Australia, the UK, Canada and the US (with New Zealand strangely excluded) – alongside Iran, Israel and North Korea – were all part of the report.
The main output, was the ranking of the nations involved, as part of a three tier assessment. The only nation to appear in “tier 1”, where the United States.
The Cyber Hut Comment
Capability or Intent?
The report is a long and detailed read and provides a good foundational understanding of the main military and foreign policy strategies as well as the more pragmatic funding and cyber structure of the leading nations. One area I thought was lacking however, was the focus on intent. Whilst the strategy and doctrine area should cover intent, intent alongside capability is really an actionable way of measuring a warfare capability.
Iran may have considerably fewer resources than the US, but does it have a higher intent to use offensive information warfare or denial of service attacks? I think intent should be analysed separately and more deeply – tying in with a general understanding of current and future foreign policy.
Does it Pay to Be Top Dog?
The US was placed top of the pops – quite correctly in many eyes. However, has that position helped or hindered it’s ability to defend itself from digital security attacks? Look at the recent attacks on the Colonial Pipeline as a good example, of attacks arguably by less able adversaries, that were able to inflict huge damage – with material impact on policy decisions and response. That is a pretty big example (and one of many undoubtedly), where asymmetry in warfare becomes more acute.
Which is Better? Defence of Attack?
Many nation states are investing heavily (in both personnel, structure and technology terms) in offensive cyber capabilities. Discussion over what offensive cyber really means (does it mean intelligence ++, “hacking the hacker”, disruption…?) continues, but many nations, including the UK – who at the end of 2020 announced the creation of it’s multi-stakeholder National Cyber Force – are attempting to leverage offensive cyber as a coercive force.
However, is defence not a more strategic position to take? Russia with it’s RuNet approach to controlling domestic ‘net access, might actually put it in a position to effectively “disconnect” the country from the internet backbone in times of all out cyber attack.
About The Author

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. He is part-time postgraduate on the GCHQ certified MSc. Information Security at Royal Holloway University, UK. His 2021 research diary focuses upon “How To Kill The Password”, “Next Generation Authorization Technology” and “How IAM Countermeasures Can Defend Against Cyberwar”. For further information see here.
