Customer, consumer and citizen identity and access management platforms are often plagued by the internal design team analysis of “should we build or buy?”. Many early CIAM projects often get labelled as “just being a login box”. How hard can that be? There are often lots of uncertainties too. How many users will register for the system? Will the service or application generate new revenue? How long will the service be needed for? What are the expected throughput and capacity levels? A lack of clarity can often result in a lack of complete requirements, a limited internal business case and limited available funding.
The ability to implement “just a login box” of course clearly misses the main features of a complete CIAM platform – which is there to drive business opportunity, through stickier customer relations via a secure, multichannel and privacy preserving service.
Why Home Grown Solutions Exist
Clearly this question assumes that a market ready commercial solution exists. Today it does – but perhaps 6-7 years ago that was not the case, allowing a home grown solution an immediate priority focus.
Small Scoped Project
Another angle to consider, is the small, highly scoped project that essentially focused on the “glueware” that integrated existing customer relationship management systems together, often with a basic external facing mobile application or web application. The requirements may also be highly customised to particular data flows, making the procurement of an off-the-shelf system too costly or time consuming.
Lack of Organisational Maturity
To buy any software – especially platform focused systems – requires a level of business maturity – especially surrounding budget ownership, metrics, deployment and accountability. The CIAM capabilities might be well defined, but a team to manage and own the platform may not exist – which limits the ability for an external product to be a) purchase and b) monitored for a return on investment.
Implications of Home Grown
Building anything in-house has implications – both good and bad.
Can The Tooling be Sold?
A simple question to try and ask, is “can the tooling that has been built in house be sold?”. The coarse grained answer of course, is typically not, but that is not to say the tooling can’t generate revenue. Clearly if the service the CIAM tooling powers is business enabling, the internal cost can often be consumed by the revenue that is generated. However, this calculation is not complete. Another subtraction must also take place – the opportunity cost associated with the internal development and maintenance team. What could they have been doing instead of building the CIAM tool? I don’t want my local doctor building the hospital website – even if he could – as the opportunity cost of course is that he is unable to see patients whilst he is coding. The same applies here.
Can it be Extended and Expanded?
It may well be a simple project to add an authentication layer to an application. But can that in turn be extended to handle multi-factor authentication? What about an end user dashboard to handle data subject access requests? What about tokenization services to handle privacy preserving data sharing use cases? Unless a long tail future roadmap was created along with a generic and modular platform, those use cases are unlikely to be added easily. The second aspect to consider, is that CIAM systems are often plagued with inaccurate user numbers – often resulting in huge spikes in demand, followed by slumps in infrastructure need. Was that considered during design of the “login box”?
A Home Grown Checklist
So how to decide? The following is a simple way of discussing the problem in house:
- Does the organisation have existing expertise in designing identity and access management capabilities?
- Does the organisation have an existing operational team to support ongoing CIAM functions?
- Does the organisation have an allocated budget for CIAM based solutions?
- Does the organisation have success metrics for systems that will use CIAM capabilities?
- Does the organisation have to adhere to external security or compliance requirements?
- Has the organisation had experience in building external facing applications?
- Is the profile of the application end users known? (Eg. volume, usage, location, growth pattern, habits)
- Are the current and future requirements for the CIAM system known? (Eg. integrations, security, usability, access control)
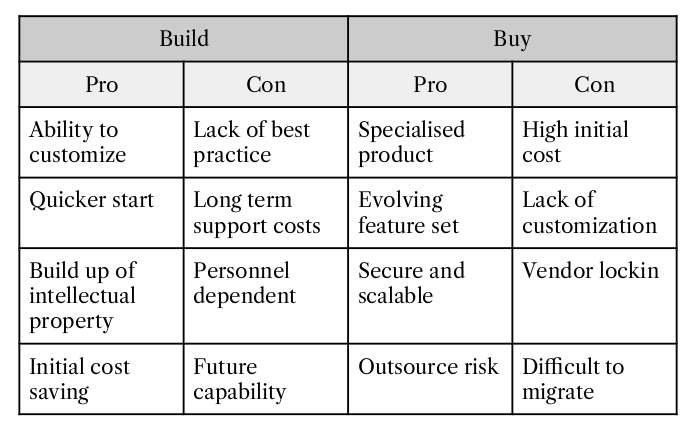
Sections of the above were taken from chapter 2 of “Consumer Identity & Access Management: Design Fundamentals” available to purchase on Amazon now.

About The Author

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. He is also a part-time postgraduate on the GCHQ certified MSc. Information Security at Royal Holloway University, UK. His 2021 research diary focuses upon “How To Kill The Password”, “Next Generation Authorization Technology” and “How IAM Countermeasures Can Defend Against Cyberwar”. For further information see here.
