A selection of curated links relating to user login and authentication security controls and threat counter measures.
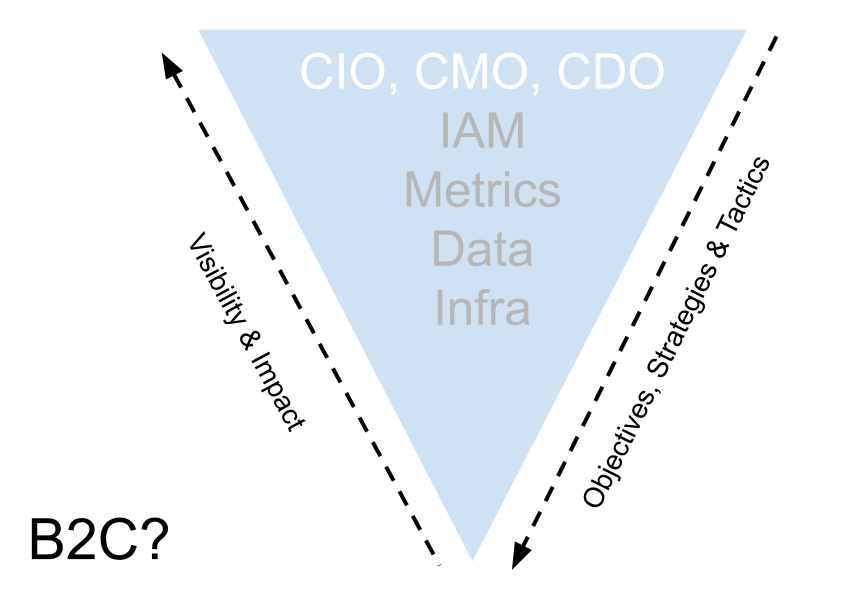
Do we need a "Chief Identity Officer"? What might drive the need for this and can existing business operating models satisfy the need for identity centric metrics?