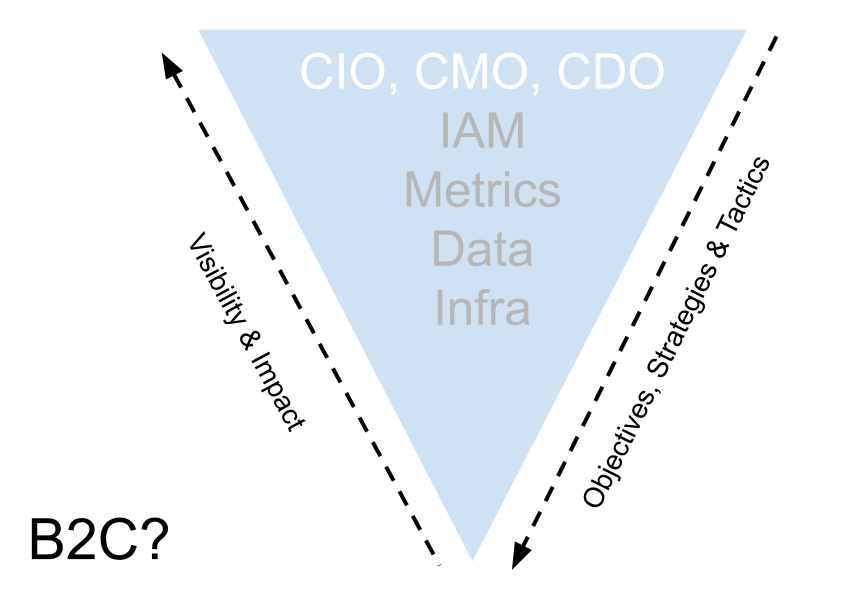
Do we need a "Chief Identity Officer"? What might drive the need for this and can existing business operating models satisfy the need for identity centric metrics?
Identity and Access Management has long been confined to two (or maybe three) buckets: B2E (employee […]
On January 26th, the US Government issued a memorandum, relating to the adoption of zero trust […]
Identity and Access Management is going through a new golden age. The movement to IAM as […]
Customer, consumer and citizen identity and access management platforms are often plagued by the internal design […]
Note the subtle play on words there? Is cyber security a huge mess of complexity or […]
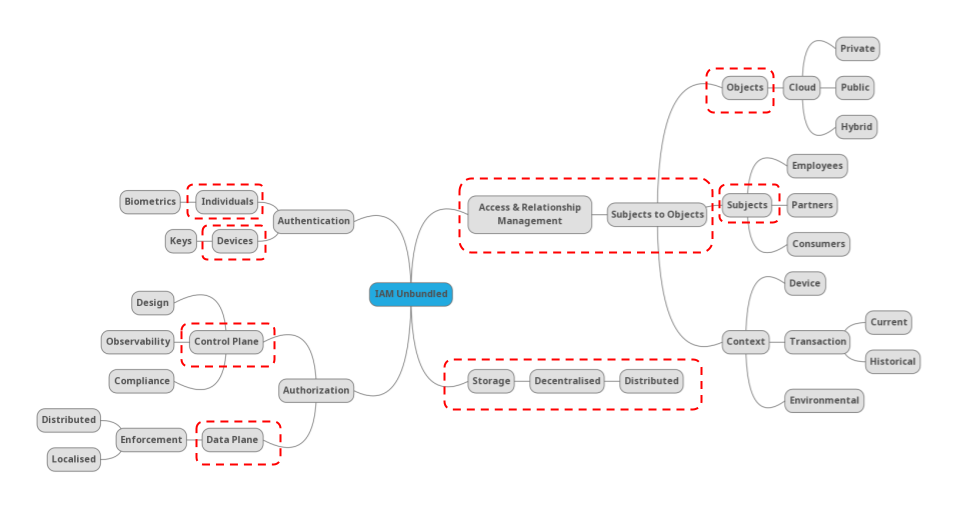
Authorization – the old chestnut often associated with role based access control – is seemingly making […]
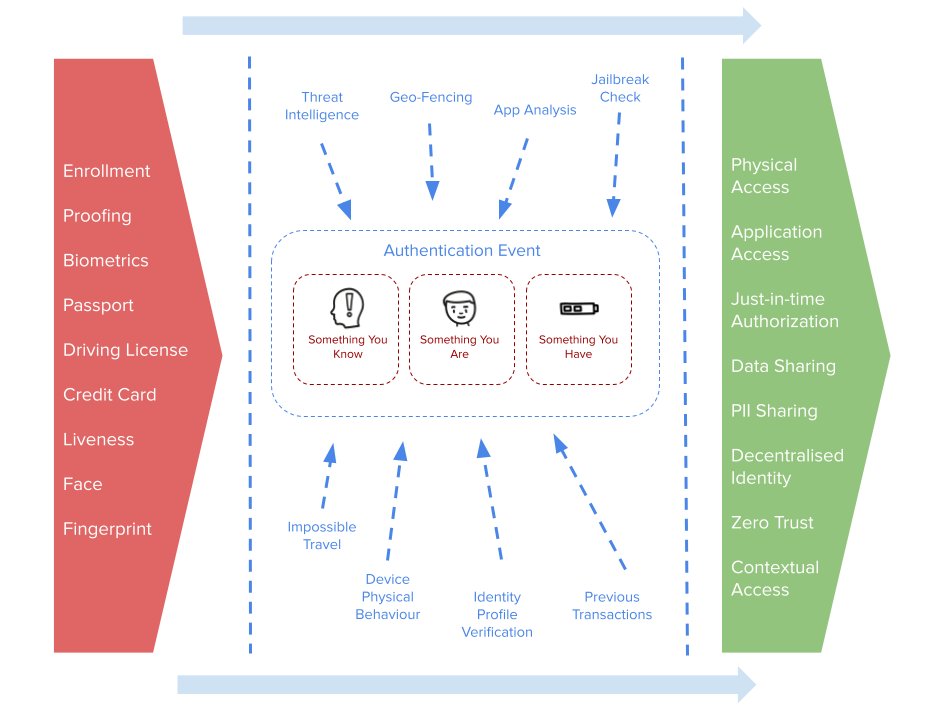
Authentication does not exist in a vacuum. It does not exist in a silo. The aim […]