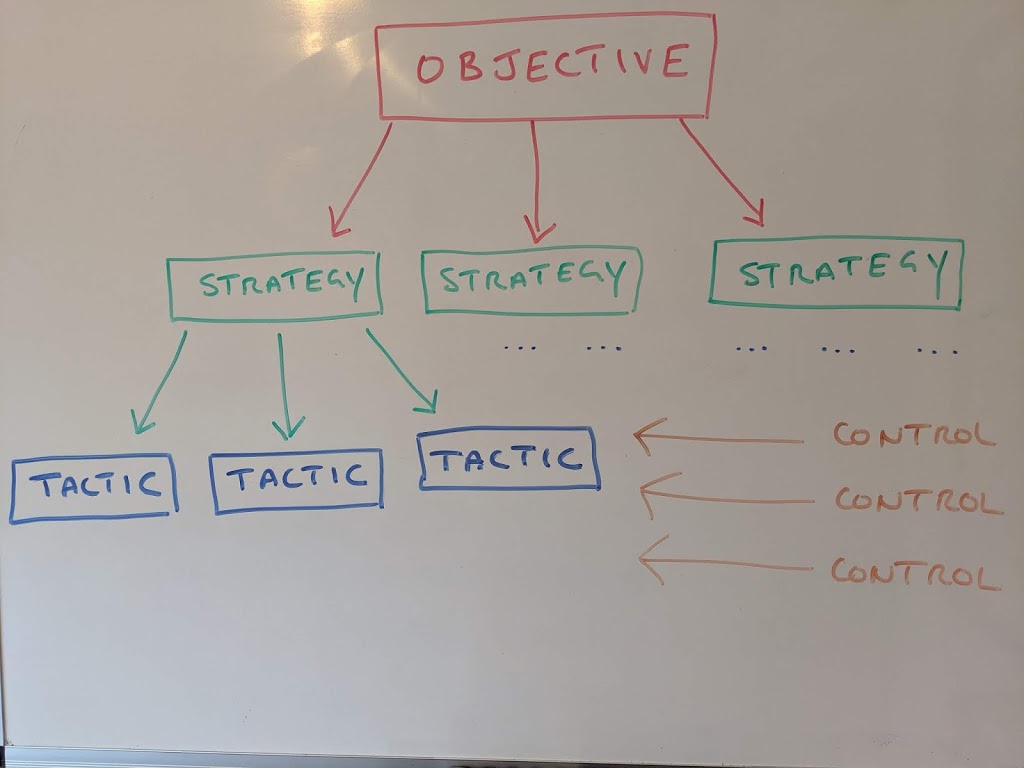
When it comes to cyber security design, there have been numerous ways of attempting to devise […]
Posts in November 2019
Registered in England & Wales as TCH Research Ltd 13188456. Registered Office: 7 Christie Way, Christie Fields, Manchester, M21 7QY, UK. Email: info@thecyberhut.com
© 2021 - 2024 The Cyber Hut.